This article explains how to configure Windows to save passwords for RDP connections and troubleshoot issues when passwords are not saved, requiring re-entry each time.
Saving Passwords for RDP Connections in Windows
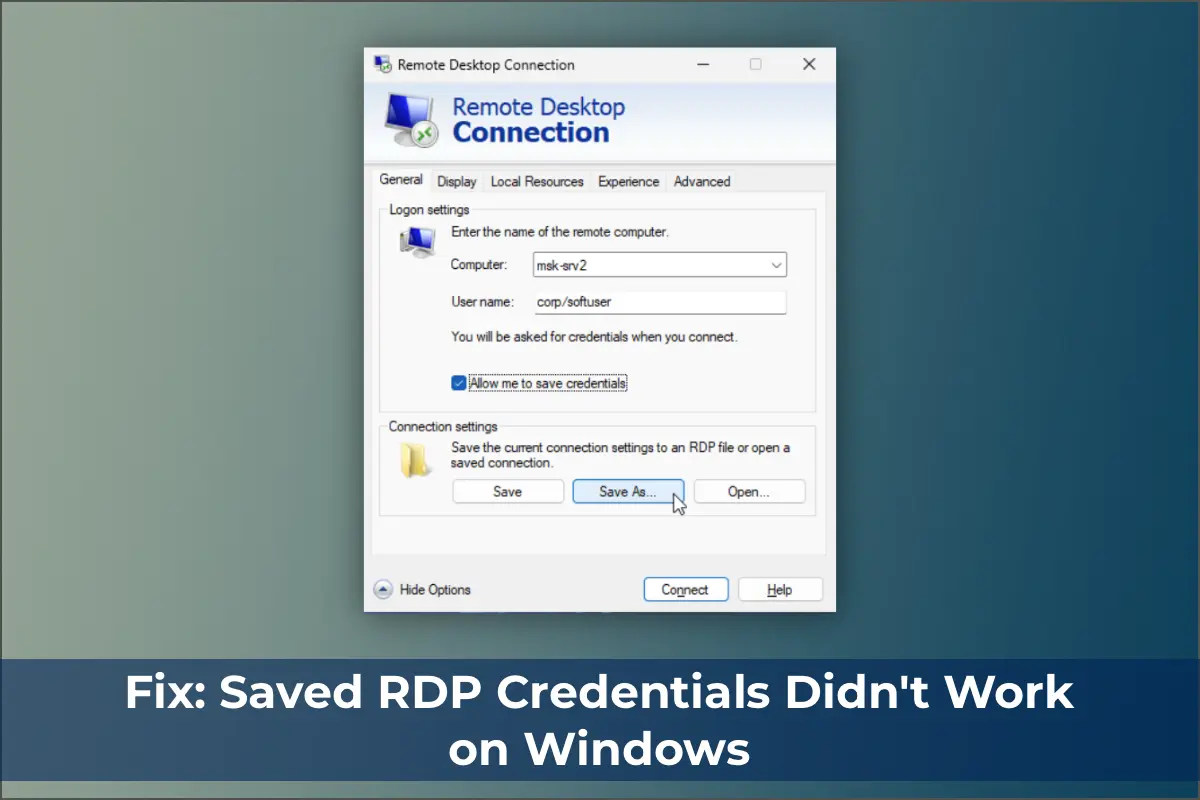
By default, Windows allows users to save passwords for RDP connections. In the Remote Desktop Connection (mstsc.exe) client, enter the remote computer’s name, credentials, and check the Allow me to save credentials option. After clicking Connect, the RDP server prompts for the password, which is stored in the Windows Credential Manager, not in the .RDP file.
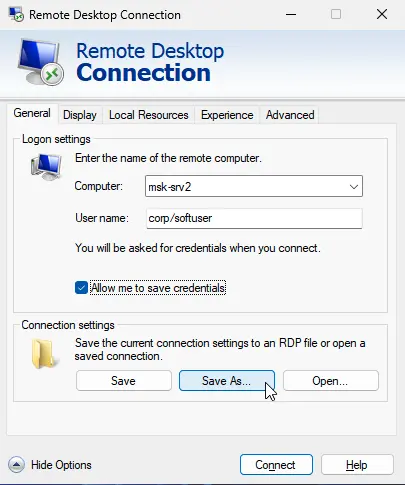
On subsequent connections, the client automatically retrieves the saved password from the Windows Credential Manager for authentication.
If a password is saved for the computer, the client window will display:
Saved credentials will be used to connect to this computer. You can edit or delete these credentials.
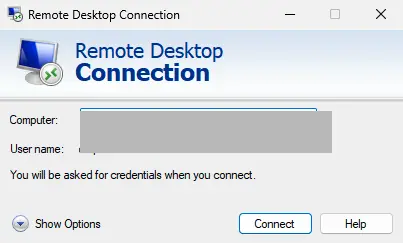
Administrators often discourage saving connection passwords in Windows. For example, in an Active Directory domain, configuring SSO (Single Sign-On) is preferred for more secure authentication.
By default, Windows does not allow saved passwords for RDP connections from a computer in an Active Directory domain to a server in another domain or workgroup. Even if the password is saved in the Credential Manager, Windows prompts for re-entry. Additionally, Windows prohibits using saved passwords for RDP when connecting with a local account instead of a domain account.
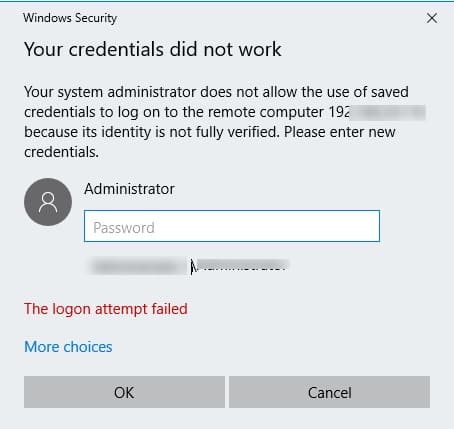
When attempting to connect with a saved password in such cases, you may encounter an error:
Your Credentials did not work
Your system administrator does not allow the use of saved credentials to log on to the remote computer CompName because its identity is not fully verified. Please enter new credentials.
Or, in the Russian version of Windows 10:
Invalid credentials
The system administrator does not allow the use of saved credentials to log on to the remote computer CompName because its identity is not fully verified. Please enter new credentials.
Windows considers such connections insecure due to the lack of trust relationships between the local computer and the remote server.
Modifying Settings to Allow Saved RDP Credentials
To change these settings on the computer initiating the RDP connection:
1. Open the Local Group Policy Editor using Win + R and the command gpedit.msc.
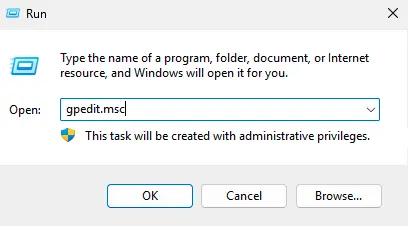
2. Navigate to Computer Configuration → Administrative Templates → System → Credentials Delegation.
3. Locate the policy Allow delegating saved credentials with NTLM-only server authentication.
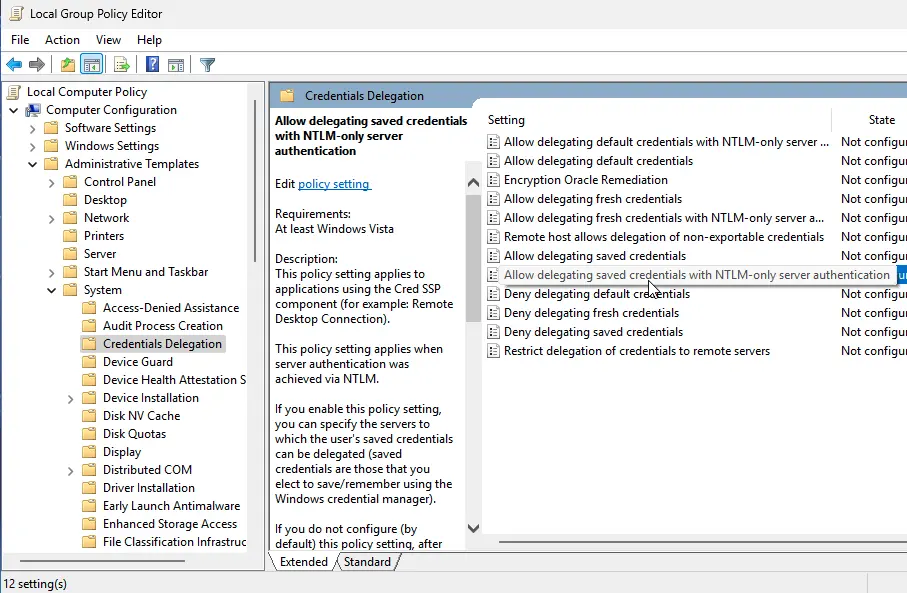
4. Double-click the policy, set it to Enabled, and click Show.
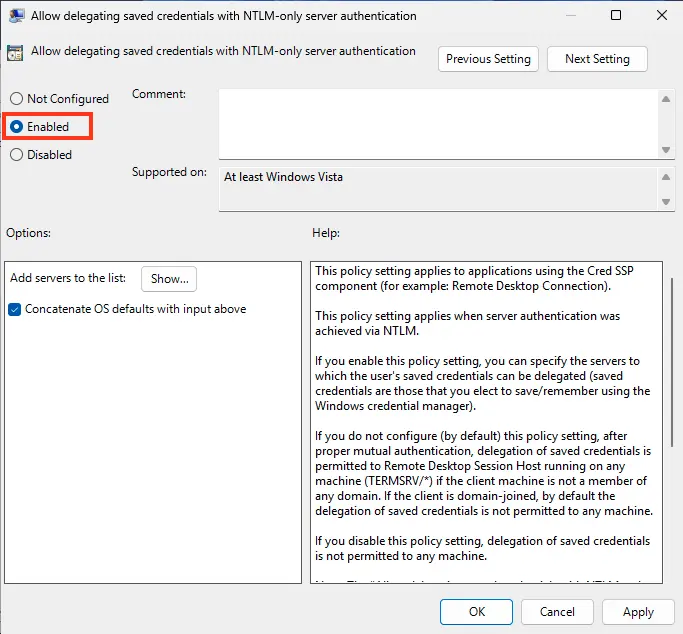
5. Specify the list of remote computers for which saved passwords can be used for RDP connections. Use the following formats:
TERMSRV/server1
— Allows connection to a specific server.
TERMSRV/*.softcomputers.org
— Allows connection to all servers in the softcomputers.org domain.
TERMSRV/*
— Allows connection to any server.
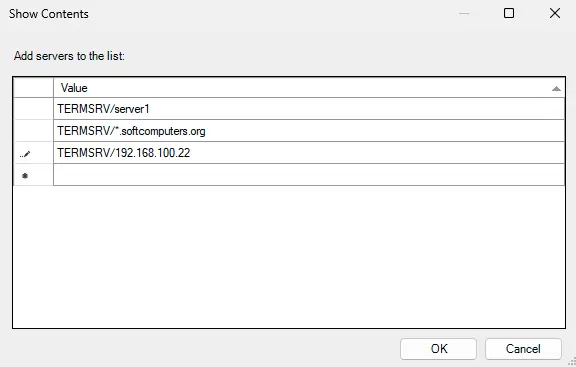
Note: TERMSRV must be in uppercase, and the server name must exactly match the one specified in the RDP client settings.
Also, add your TERMSRV/ values to the Allow Delegating Saved Credentials policy.
These settings can be applied via the registry:
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CredentialsDelegation] "AllowSavedCredentialsWhenNTLMOnly"=dword:00000001
"AllowSavedCredentials"=dword:00000001
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CredentialsDelegation\AllowSavedCredentialsWhenNTLMOnly] "1"="TERMSRV/*"
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CredentialsDelegation\AllowSavedCredentials] "1"="TERMSRV/*"
[HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Policies\Microsoft\Windows\CredentialsDelegation] "AllowSavedCredentialsWhenNTLMOnly"=dword:00000001
"AllowSavedCredentials"=dword:00000001
[HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Policies\Microsoft\Windows\CredentialsDelegation\AllowSavedCredentialsWhenNTLMOnly] "1"="TERMSRV/*"
[HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Policies\Microsoft\Windows\CredentialsDelegation\AllowSavedCredentials] "1"="TERMSRV/*"
Ensure the Deny delegating saved credentials policy is disabled or not configured, as denying policies take precedence over allowing policies.
Also, disable the Network access: Do not allow storage of passwords and credentials for network authentication policy (Computer Configuration → Windows Settings → Security Settings → Local Policies → Security Options). If enabled, attempting to save a password will result in an error:
Credential Manager Error
Unable to save credentials. To save credentials in this vault, check your computer configuration.
Error code: 0x80070520
Error Message: A specified logon session does not exist. It may already have been terminated.
Save changes and update group policies using the command:
gpupdate /force
The mstsc client should now use saved passwords for RDP connections.
Viewing and Deleting Saved RDP Passwords
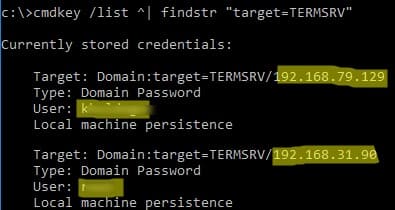
To view the list of saved passwords for RDP connections, run:
cmdkey /list ^| findstr "target=TERMSRV"
To delete saved passwords, run:
For /F "tokens=1,2 delims= " %G in ('cmdkey /list ^| findstr "target=TERMSRV"') do cmdkey /delete %H
The Local Group Policy Editor applies settings to a single computer. To apply policies to multiple computers in a domain, use domain policies via the gpmc.msc console.
Troubleshooting RDP Password Not Saving
If the settings are configured as instructed but the system still prompts for a password on each connection, check the following:
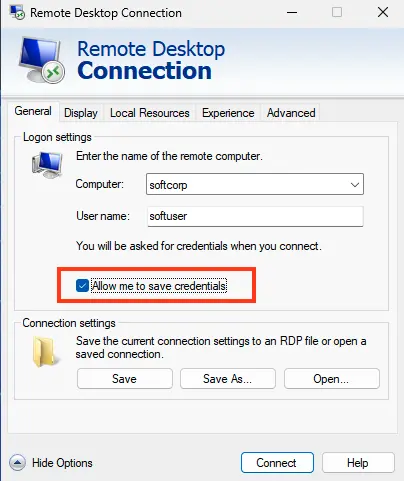
1. In the RDP settings, ensure the Always ask for credentials option is not selected.
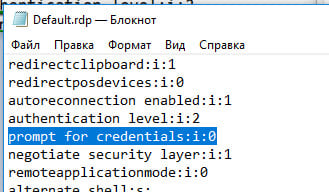
2. If using a saved .RDP file, verify that the prompt for credentials parameter is set to 0 (prompt for credentials:i:0).
3. In the Local Group Policy Editor (gpedit.msc), navigate to Computer Configuration → Administrative Templates → Windows Components → Remote Desktop Services → Remote Desktop Connection Client. Ensure the Do not allow passwords to be saved and Prompt for credentials on the client computer policies are disabled or not configured. Check the resultant policy on your computer using the gpresult command.
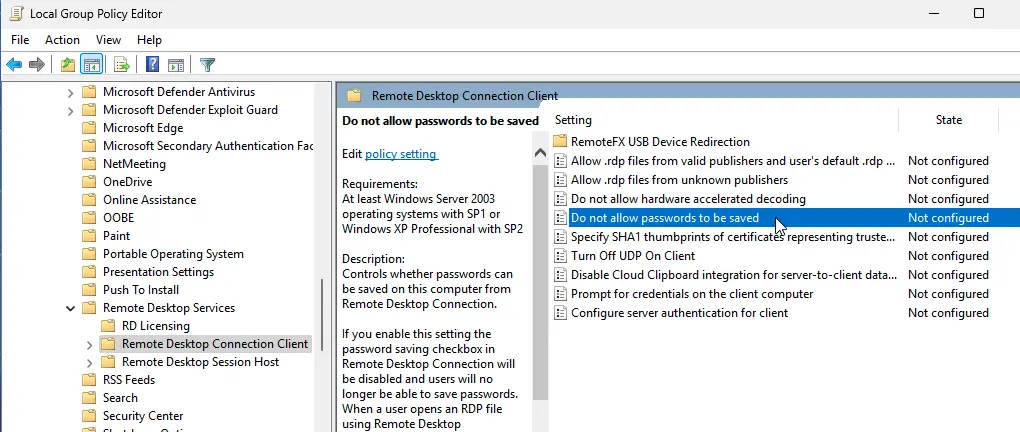
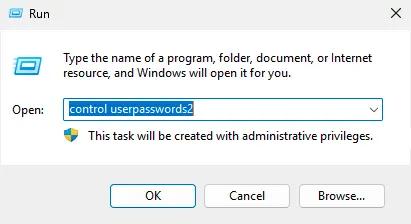
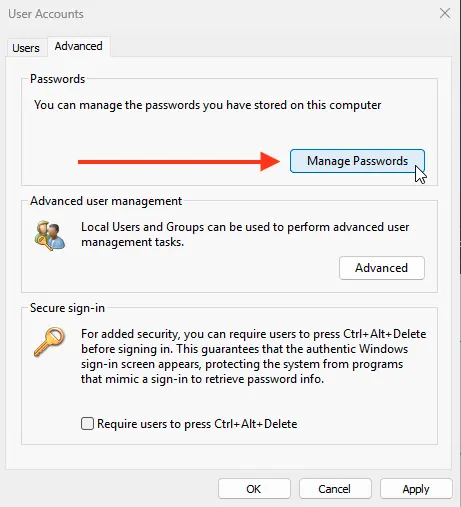
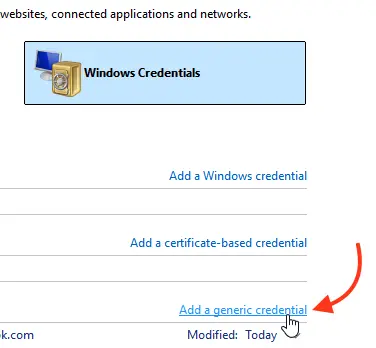
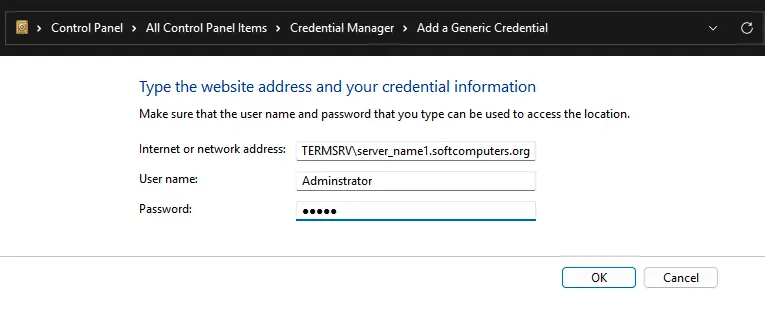
4. Delete all saved passwords in the Windows Credential Manager. Run control userpasswords2, go to the Advanced tab, and click Manage Passwords. In the opened window, select Windows Credentials and remove all saved RDP passwords (starting with TERMSRV/…).
From this window, you can manually add credentials for RDP connections. The server name must be in the format TERMSRV\server_name1. After clearing the RDP connection history, ensure saved passwords are removed.
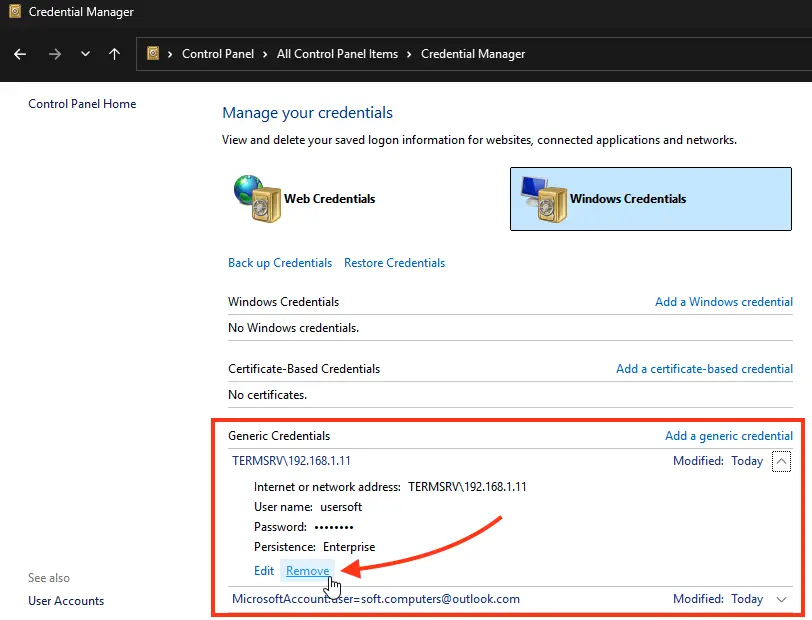
You can also manually add RDP credentials from this window. Ensure the remote RDP server name is specified as TERMSRV\server_name1. When clearing RDP connection history, remember to remove saved passwords.
Connections with saved passwords will not work if the RDP server is outdated and triggers a CredSSP encryption oracle remediation error.
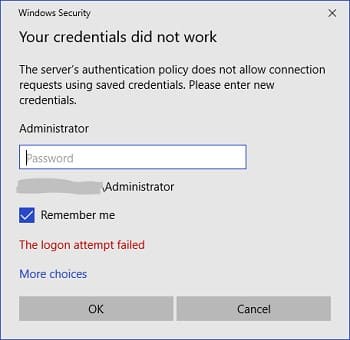
Server Authentication Policy Blocking Saved Credentials
When connecting to an RDP host using a saved password, you may encounter the error:
Windows Security
Your credentials did not work
The server’s authentication policy does not allow connection requests using saved credentials. Please enter new credentials.
To resolve this, on the remote server, disable the Always prompt for password upon connection policy in Computer Configuration → Administrative Templates → Windows Components → Remote Desktop Services → Remote Desktop Session Host → Security.
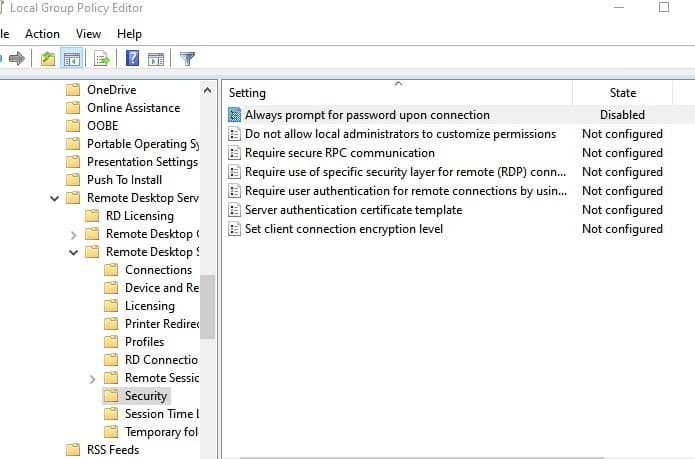
If this policy is enabled, the RDP server will always prompt for a password.
This setting can be disabled via the registry:
REG add "HKLM\SOFTWARE\Policies\Microsoft\Windows NT\Terminal Services" /v fPromptForPassword /t REG_DWORD /d 0 /f
Windows Defender Credential Guard Blocking Saved Credentials
After updating to Windows 11 22H2, users often report that saved passwords for RDP connections do not work:
Windows Security: Your credentials did not work
Windows Defender Credential Guard does not allow using saved credentials. Please enter your credentials.

Introduced in Windows 10 1607, Windows Defender Remote Credential Guard protects credentials during RDP connections. In the 22H2 update, saved credentials are allowed by default only with Kerberos authentication. If Kerberos is unavailable (e.g., domain controller is inaccessible or connecting to a workgroup), Remote Credential Guard blocks NTLM authentication.
To disable Credential Guard, run the following registry command:
New-ItemProperty -Path "HKLM:\System\CurrentControlSet\Control\LSA" -Name "LsaCfgFlags" -PropertyType "DWORD" -Value 0 -Force
After completing these steps, users should be able to use saved passwords for RDP connections.