The Read-Only Domain Controller (RODC) was first introduced in Windows Server 2008 and continues to be supported in Windows Server 2012 R2, 2016, 2019, and 2022. The primary purpose of an RODC is to enhance security for domain controllers in remote branches or offices with poor WAN connectivity or limited physical server security. An RODC holds a read-only copy of the Active Directory database, preventing data changes even if an attacker gains physical access to the server. This article explains the installation and configuration of an RODC in Windows Server 2019 and 2022.
You can purchase original Windows Server product keys from our store from 10.80 €
Download Windows Server installers from our catalog.
What is a Read-Only Domain Controller (RODC)?
Key differences between an RODC and a standard Read-Write Domain Controller (RWDC):
– RODC stores a read-only copy of the Active Directory database.
– It does not replicate AD data or the SYSVOL folder to other domain controllers (uses one-way replication).
– RODC stores a copy of the AD database without password hashes or other sensitive data (Filtered Attribute Set — FAS).
– RODC can cache credentials for specific users, speeding up authentication.
– When an RODC receives an authentication request, it forwards it to the nearest RWDC.
– RODC can provide administrative access without granting rights to other domain controllers or Domain Admins.
– DNS on an RODC operates in read-only mode.
Requirements for Deploying an RODC
1. Assign a static IP address.
2. Properly configure Windows Firewall or disable it.
3. Set the nearest RWDC as the DNS server.
4. RODC can be installed on both Full GUI and Core editions of Windows Server.
5. Avoid placing an RODC in the same site as an RWDC.
Installing RODC via Server Manager
1. Open Server Manager and add the Active Directory Domain Services role.
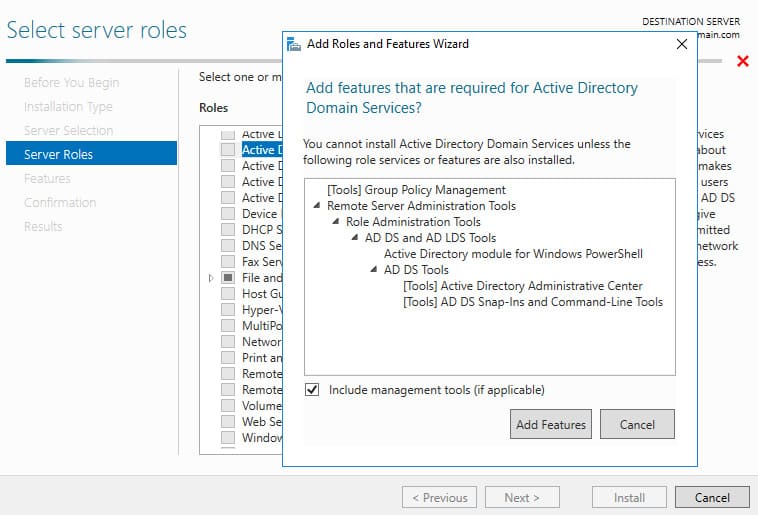
2. During the configuration of the new domain controller, select:
– Add a domain controller to an existing domain.
– Specify the domain name and domain administrator credentials.
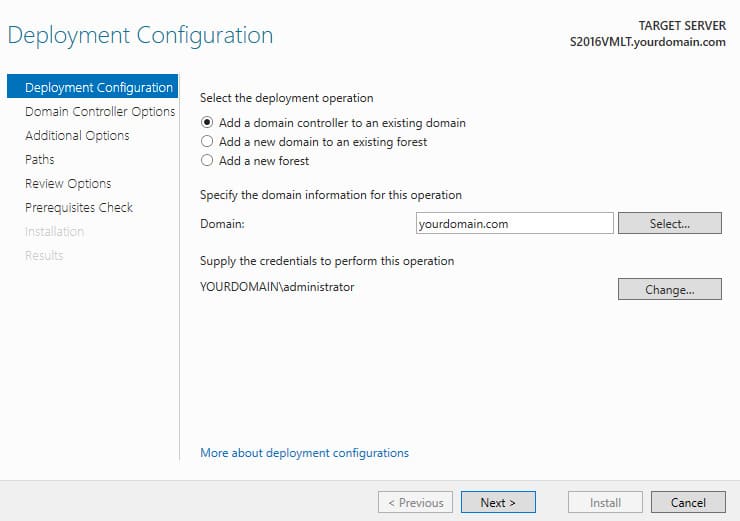
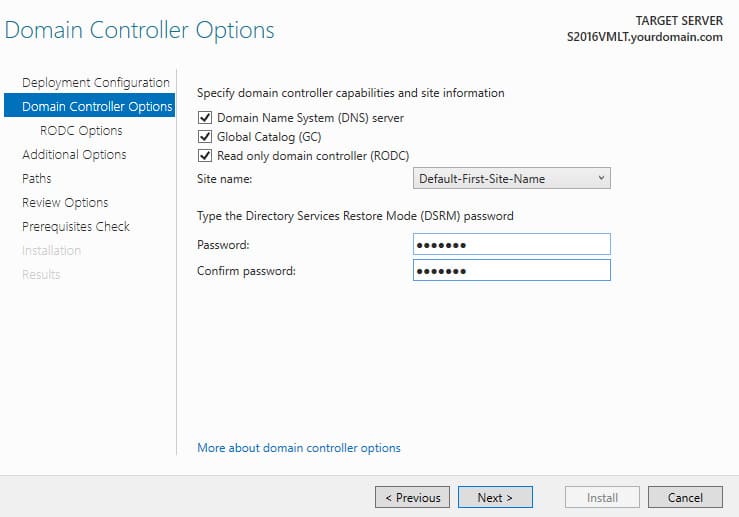
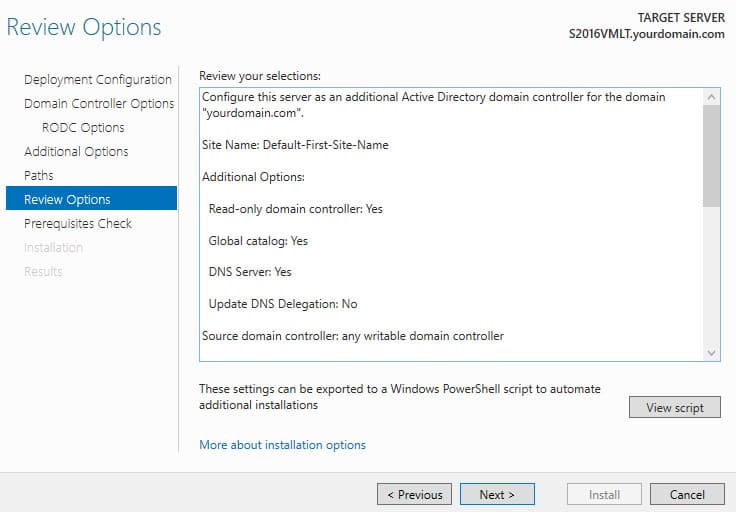
3. Specify that the DNS server role, Global Catalog (GC), and RODC should be installed. Select the AD site and set a password for Directory Services Restore Mode (DSRM).
4. Configure the following:
– The administrator who will have access to the RODC.
– Accounts allowed or denied to replicate their passwords to this RODC.
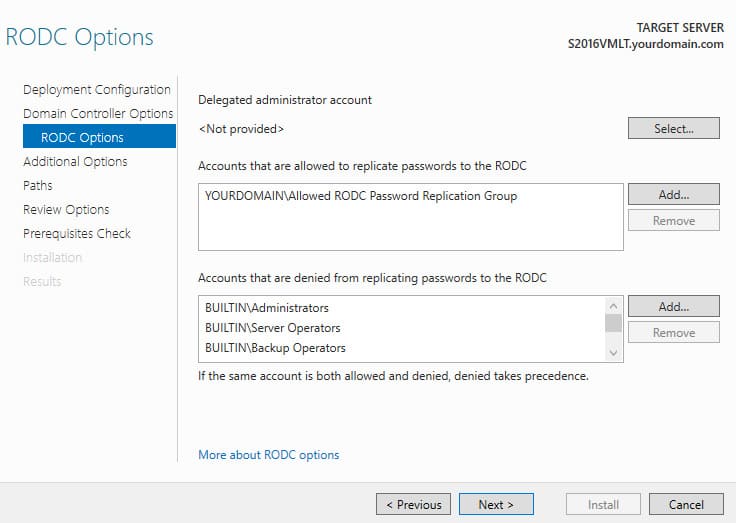
5. Specify that the AD database can be replicated from any domain controller: Replicate from -> Any domain controller.
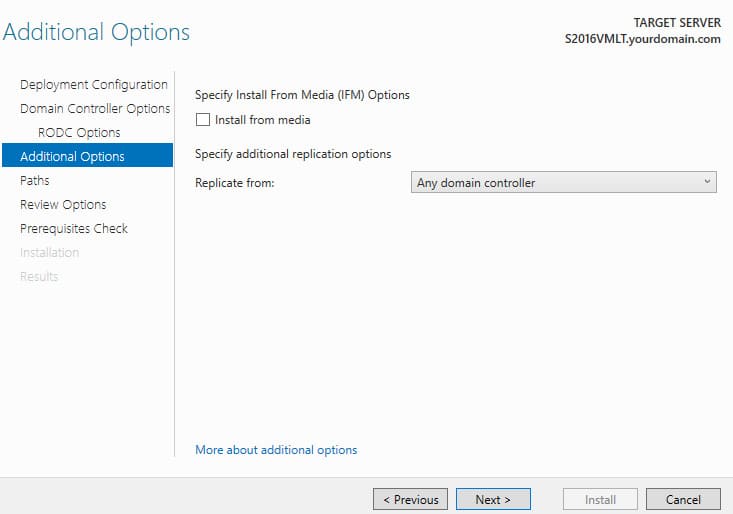
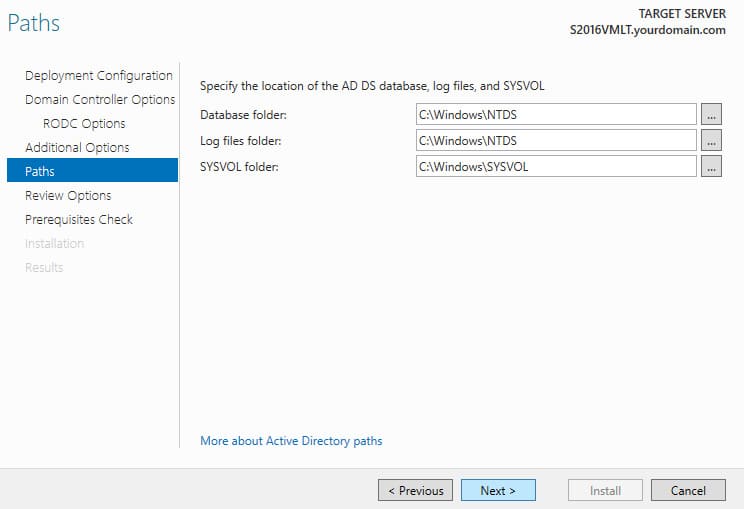
6. Specify the paths for the NTDS database and SYSVOL folder.
7. After verifying the settings, proceed with the RODC installation.
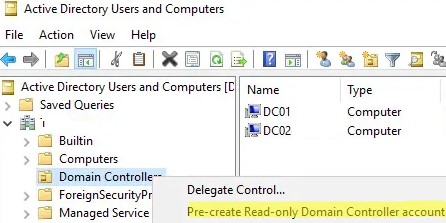
8. Alternatively, you can use the Staged option, which involves pre-creating the RODC computer account via the Active Directory Users and Computers (ADUC) console. Right-click the Domain Controllers container and select Pre-create Read-Only Domain Controller account.
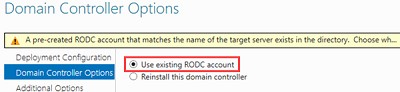
When installing ADDS on a server with the same name, you’ll see the message:
A Pre-created RODC account that matches the name of the target server exists in the directory. Choose whether to use this existing RODC account or reinstall this domain controller.
Select Use existing RODC account to use the pre-configured RODC account in AD.
After completing the role installation and rebooting the server, you’ll have a fully functional RODC.
When connecting to the RODC via the ADUC console (dsa.msc), all buttons for creating new AD objects will be disabled (grayed out). You also cannot modify object attributes on an RODC. All other actions in the Active Directory console, including searches, work as usual.
Installing RODC with PowerShell
1. Install the necessary components using PowerShell:
Add-WindowsFeature AD-Domain-Services, RSAT-AD-AdminCenter, RSAT-ADDS-Tools
2. Start the RODC installation:
Install-ADDSDomainController -ReadOnlyReplica:$true -DomainName yourdomain.com -SiteName "Default-First-Site-Name" -InstallDns:$true -NoGlobalCatalog:$false
The system will prompt for a reboot upon completion.
3. To check the status of domain controllers in the domain, run:
Get-ADDomainController -Filter * | Select-Object Name,IsReadOnly
For an RODC, the IsReadOnly attribute should be True. To list only RODCs:
Get-ADDomainController –filter {IsReadOnly –eq $true}
4. To pre-create an RODC account in the domain:
Add-ADDSReadOnlyDomainControllerAccount -DomainControllerAccountName SPB-RO-DC1 -DomainName winitpro.ru -DelegatedAdministratorAccountName "winitpro\kbuldogov" -SiteName SPB_RO_Site
5. When promoting the server to a domain controller, use:
Install-ADDSDomainController -DomainName winitpro.ru -Credential (Get-Credential) -LogPath "C:\Windows\NTDS" -SYSVOLPath "C:\Windows\SYSVOL" -ReplicationSourceDC "SPB-DC01.winitpro.ru" – UseExistingAccount
You cannot modify AD object attributes when connected to an RODC via PowerShell. To modify attributes from a site with an RODC, specify the nearest RWDC using the –Server parameter, available in cmdlets like Set-ADUser, Set-ADComputer, New-ADUser, etc.
Replication and Password Caching Policies on RODC
Each RODC can have a defined list of users, computers, and servers whose password hashes can or cannot be replicated to the domain controller.
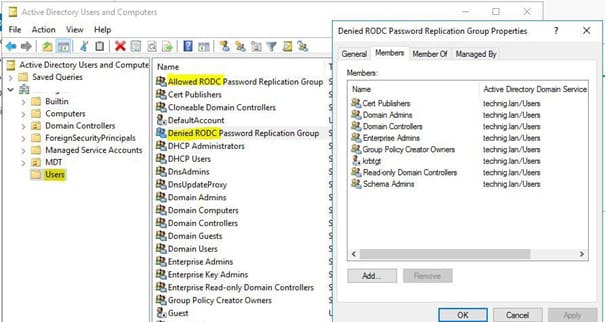
By default, two global groups are created in the domain:
– Allowed RODC Password Replication Group — groups and users whose passwords can be cached.
– Denied RODC Password Replication Group — contains administrative groups whose passwords cannot be cached.
The first group is empty by default, while the second includes administrative security groups to prevent password replication and caching on RODCs, reducing the risk of compromise. These groups include by default:
– Group Policy Creator Owners
– Domain Admins
– Cert Publishers
– Enterprise Admins
– Schema Admins
– krbtgt account
– Account Operators
– Server Operators
– Backup Operators
The Allowed RODC Password Replication Group typically includes user groups from the branch where the RODC is located.
If multiple RODCs are deployed in the domain, it’s best to create such groups for each RODC. Group assignment to an RODC is configured in the server’s properties in the ADUC console under the Password Replication Policy tab.
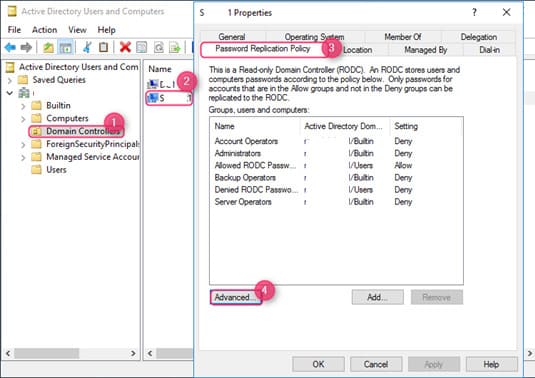
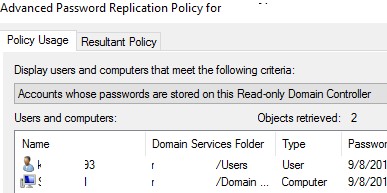
In the Advanced Password Replication Policy for RODC_name window, you can view:
– Accounts whose passwords are stored on this Read-Only Domain Controller — list of users and computers whose passwords are cached on this RODC.
– Accounts that have been authenticated to this Read-Only Domain — list of users and computers connected through this RODC.
1. Manage RODC groups using PowerShell. List users in an AD group:
Get-ADGroupMember -Identity "Denied RODC Password Replication Group" | ft Name, ObjectClass
2. Add all active users from a specific Active Directory OU to the RODC group:
Get-ADUser -Filter {Enabled -eq "True"} -SearchBase 'OU=SPBOffice,DC=winitpro,DC=ru' | ForEach-Object {Add-ADGroupMember -Identity 'Allowed RODC Password Replication Group' -Members $_ -Confirm:$false}
3. To cache user passwords on the RODC, run the script:
$users = Get-ADUser -Filter {Enabled -eq "True"} -SearchBase 'OU=SPBOffice,DC=winitpro,DC=ru'
foreach ($user in $users) {
Get-ADObject -identity $user | Sync-ADObject -Source SPB-DC01 ‑Destination SPB-RO-DC1 -PasswordOnly
}
4. To check if user passwords are cached on the RODC, run:
Get-ADDomainControllerPasswordReplicationPolicyUsage -Identity SPB-RO-DC1 ‑RevealedAccounts
Using an RODC enables secure deployment of domain controllers in remote offices and branches, ensuring reliable AD operation and reducing the risk of data compromise in case of physical server access.