The Azure Active Directory (Azure AD) password policy defines requirements for user passwords in a tenant, including password complexity, length, expiration settings, account lockout policies, and other parameters. This article explains how to manage password policies in Azure AD.
By default, a standard password policy applies to all cloud-created accounts in Azure AD (not synchronized from on-premises Active Directory via Azure AD Connect).
Default Password Policy Settings
1. Allowed characters: A-Z, a-z, 0-9, space, and special characters @ # $ % ^ & * – _ ! + = [ ] { } | \ : ‘ , . ? / ` ~ ” ( ) ;
2. Password complexity: At least three of the four character groups (uppercase, lowercase, digits, special characters)
3. Password length: Minimum 8 characters, maximum 256 characters
4. Prohibition of previously used passwords
Table of Contents
1. Password Expiration in Azure AD
2. User Lockout in Azure AD
3. Banning Common Passwords in Azure AD
Password Expiration in Azure AD
By default, passwords in Azure AD (Microsoft 365) do not expire. However, you can enable password expiration via the Microsoft 365 Admin Center:
1. Navigate to Microsoft 365 Admin Center > Settings > Security & Privacy > Password expiration policy.
2. Disable the Set password to never expire (recommended) option.
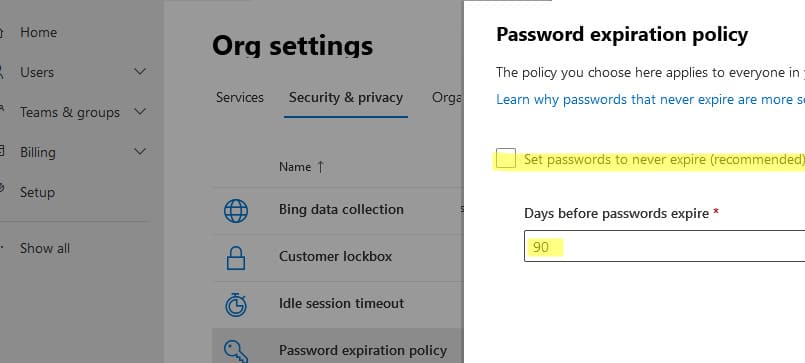
Azure AD Password Expiration Policy
– Password expiration: 90 days
– Notification for password change: Starts 14 days before expiration
Microsoft recommends avoiding password expiration for users with MFA authentication enabled.
You can modify password expiration settings using the MSOnline PowerShell module:
1. Install the module (if needed) and connect to your tenant:
Install-Module MSOnline
Connect-MsolService
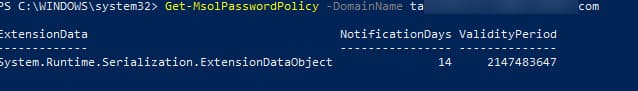
2. View current password expiration policy settings:
Get-MsolPasswordPolicy -DomainName softcomputers.com
3. Modify the password expiration period and notification days:
Set-MsolPasswordPolicy -DomainName softcomputers.org -ValidityPeriod 180 -NotificationDays 21
You can also manage password expiration settings for specific users using the Azure AD module:
1. Connect to Azure AD:
Connect-AzureAD
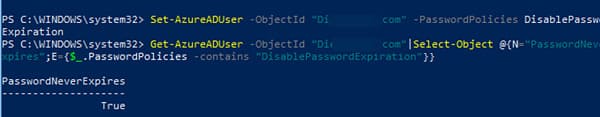
2. Enable the Password never expires option for a specific user:
Set-AzureADUser -ObjectId "DimovS@softcomputers.org" -PasswordPolicies DisablePasswordExpiration
3. View password expiration details for a user:
Get-AzureADUser -ObjectId "DimovS@softcomputers.org" | Select-Object @{N="PasswordNeverExpires";E={$_.PasswordPolicies -contains "DisablePasswordExpiration"}}
4. Enable password expiration for a user:
Set-AzureADUser -ObjectId "DimovS@softcomputers.org" -PasswordPolicies None
User Lockout in Azure AD
Another aspect of Azure AD password policy is configuring user lockout for incorrect password attempts.
By default, an account is locked for 1 minute after 10 failed authentication attempts. The lockout duration increases with each subsequent failed attempt.
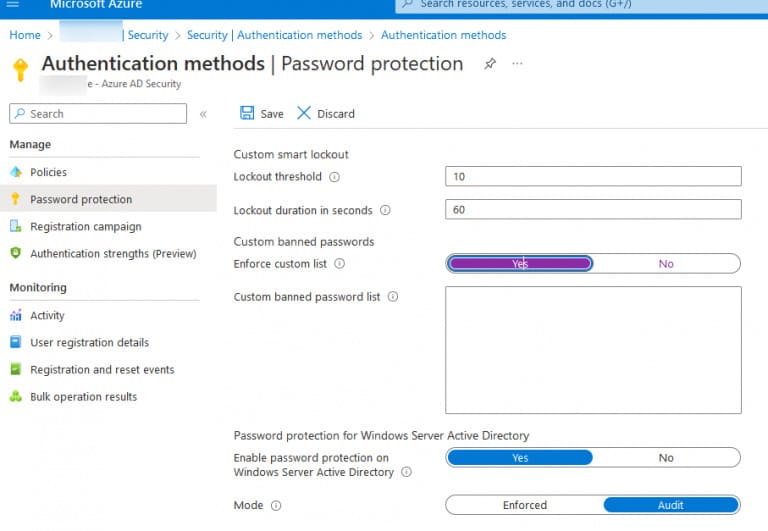
Lockout settings are located in Azure Portal > Azure Active Directory > Security > Authentication methods > Password protection.
Lockout Settings
1. Lockout threshold: Number of failed password attempts before account lockout (default: 10).
2. Lockout duration in seconds: Duration of the lockout (default: 60 seconds).
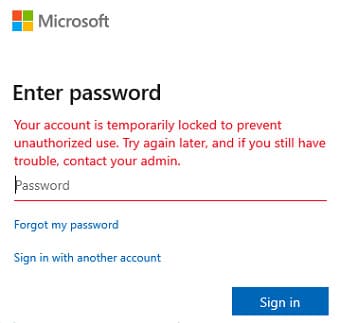
When an account is locked, the user sees the following message:
Your account is temporarily locked to prevent unauthorized use. Try again later, and if you still have trouble, contact your admin.
Banning Common Passwords in Azure AD
Azure AD’s Password Protection feature prevents the use of weak or commonly known passwords, such as P@ssw0rd or Pa$$word.
To configure this feature:
1. Navigate to Azure Active Directory > Security > Authentication methods > Password protection.
2. Enable the Enforce custom list option in the Custom banned list section and add up to 1000 passwords to block.
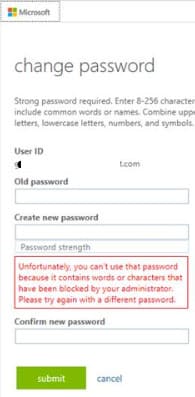
If a user attempts to set a banned password, they will see:
Unfortunately, you can’t use that password because it contains words or characters that have been blocked by your administrator. Please try again with a different password.
For on-premises Active Directory Domain Services (AD DS):
1. Requires an Azure AD Premium P1 or P2 subscription.
2. Enable the Enable password protection on Windows Server Active Directory option.
3. Install the Azure AD Password Protection service and agent on all domain controllers.
4. Enable the EnforceCloudPasswordPolicyForPasswordSyncedUsers option to apply Azure’s password policy to synchronized users from AD DS.
Azure AD provides flexible and robust tools for managing user passwords, including lockout policies, password expiration settings, and restrictions on weak passwords. Using these tools enhances security and helps prevent unauthorized access to corporate resources.