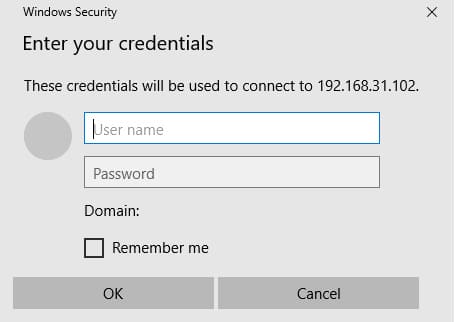
Basic Authentication – this authentication type is familiar to many Windows users. Basic Authentication uses a simple Windows Security window prompting for a username and password, with the option to save the password in the Windows Credential Manager. Key drawbacks of Basic Authentication:
– Does not support Multi-Factor Authentication (MFA).
– Vulnerable to brute-force password attacks.
– Applications store and use user credentials in plain text.
Modern Authentication is based on Active Directory Authentication Library (ADAL) and OAuth 2.0 protocols. Key benefits of Modern Authentication:
– Does not require storing user credentials in applications.
– Uses time-limited tokens for authentication.
– Supports additional authentication factors, such as MFA.
The login window for username and password appears when connecting to Microsoft 365 or Azure services, including connections via PowerShell.
Finding Microsoft 365 Applications Using Basic Authentication
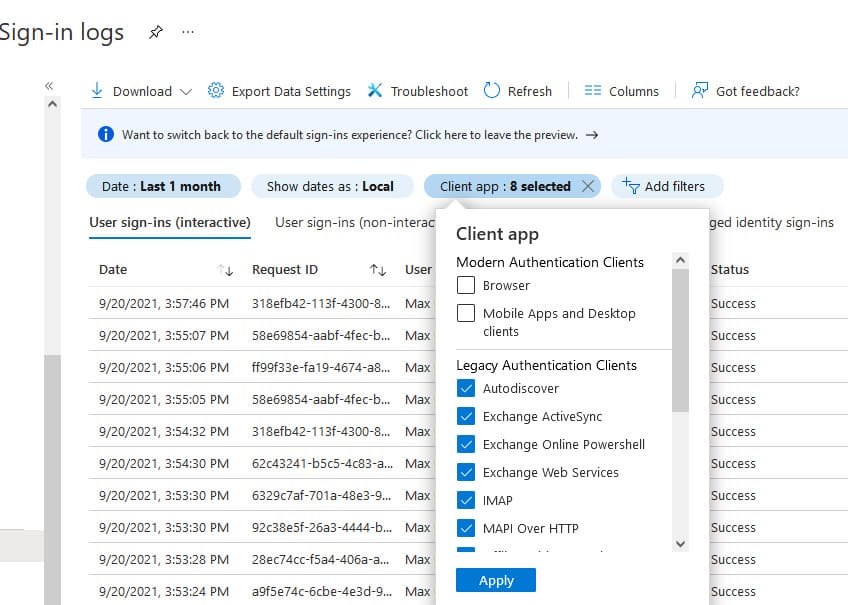
Before enabling Modern Authentication and disabling Basic Authentication, you need to identify which users and applications still rely on Basic Authentication.
– Open the Azure management portal.
– Navigate to Azure Active Directory -> Sign-in logs.
– Select the time range Last 1 month.
– Add a filter for the Client App field.
– Select all Legacy Authentication Clients.
This process will help identify users and applications still using Basic Authentication, allowing you to migrate them to Modern Authentication.
Microsoft Announced the Disabling of Basic Authentication
Microsoft plans to automatically disable Basic Authentication for tenants where it is not in use, starting from February 2023.
How to Enable Modern Authentication for a Microsoft 365 Tenant?
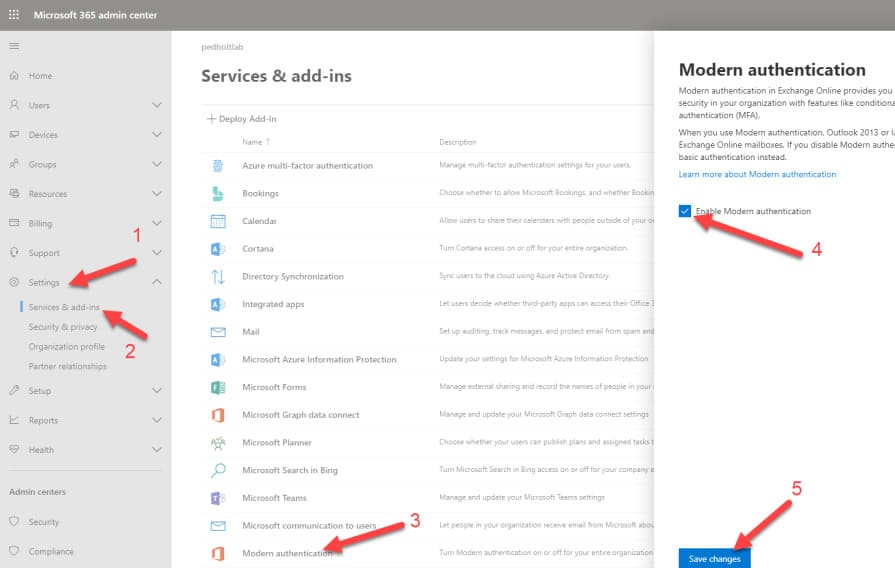
Modern Authentication can be enabled through the Microsoft 365 Admin Center:
– Go to https://admin.microsoft.com.
– Navigate to Settings -> Org Settings -> Modern authentication.
– Enable the option Turn on modern authentication for Outlook 2013 for Windows and later.
– Save the changes.
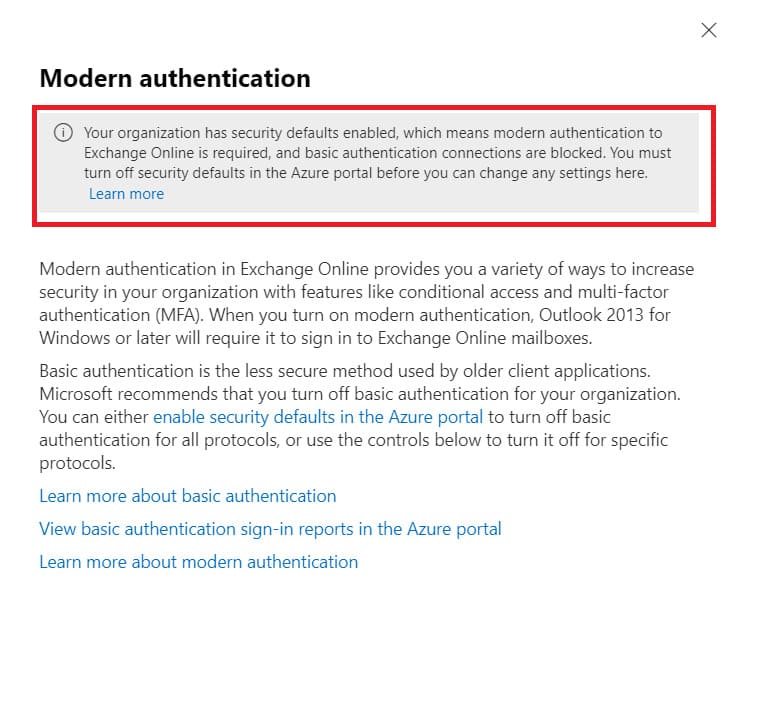
For new Office 365 tenants, Modern Authentication is enabled by default, and Basic Authentication is already disabled.
Enabling Support for Basic Auth for a Tenant
If needed, Basic Authentication support can be enabled via the Azure portal:
– Navigate to Azure Active Directory -> Properties -> Manage Security defaults.
– Set Enable Security defaults = No.
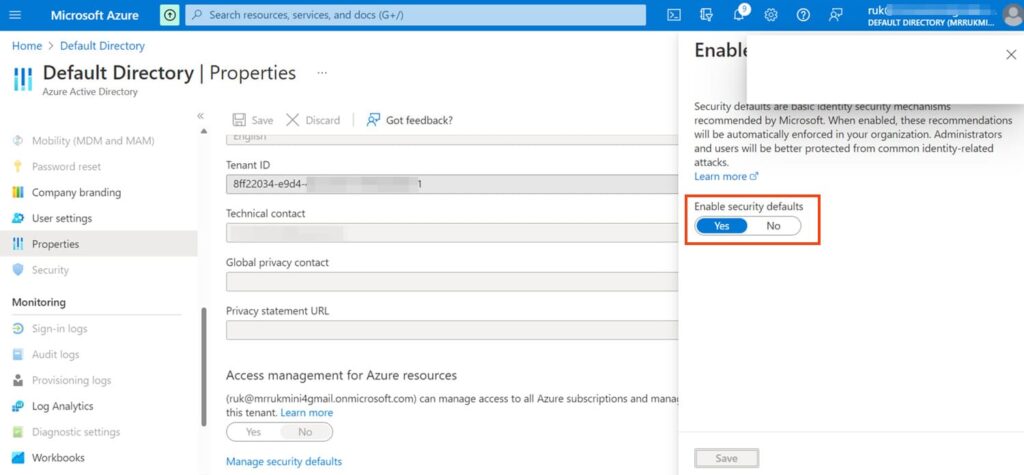
– In the Allow access to basic authentication protocols section, select the applications for which Basic Authentication is permitted:
– Outlook client
– Exchange ActiveSync (EAS)
– Autodiscover
– IMAP4
– POP3
– Authenticated SMTP
– Exchange Online PowerShell (only EXOv2 supports Modern Authentication)
– Disable Basic Auth for all applications where it is not needed.
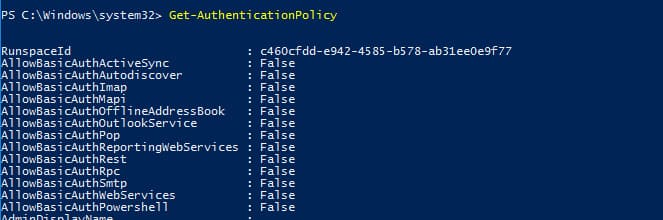
Checking Current Authentication Settings with PowerShell
To display current settings and permitted protocols, use the following PowerShell commands:
Get-AuthenticationPolicy
Get-AuthenticationPolicy -AllowBasicAuth
Creating and Applying Authentication Policies
To enhance security, you can create a dedicated policy allowing Basic Authentication for specific protocols:
– Create a policy:
Set-AuthenticationPolicy -Identity "BasicAuthAllowPoSh" -AllowBasicAuthPowershell:$true
– Apply the policy to a user:
Set-User -Identity kbuldogov -AuthenticationPolicy "BasicAuthAllowPoSh"
– Create a default policy to block legacy protocols:
New-AuthenticationPolicy -Name "BasicAuthBlock"
Set-OrganizationConfig -DefaultAuthenticationPolicy "Block Legacy Authentication"
Verifying Modern Authentication Status
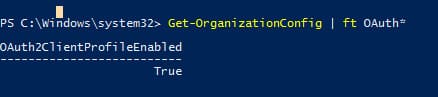
Ensure Modern Authentication is enabled for the tenant:
Get-OrganizationConfig | ft OAuth*
If OAuth2ClientProfileEnabled = False, Modern Authentication is disabled.
Support for Modern Authentication in Different Outlook Versions
Consider the specifics of Modern Authentication support across Outlook versions:
Outlook 2010 and earlier: Do not support Modern Authentication. If Basic Auth is disabled, these versions cannot connect to Exchange Online.
Outlook 2013: Requires registry settings to support OAuth:
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\15.0\Common\Identity
– EnableADAL = 1
– Version = 1
Outlook 365, 2019, 2016: Modern Authentication is supported by default. To ensure consistent use of Modern Authentication, set the registry parameter AlwaysUseMSOAuthForAutoDiscover = 1:
HKEY_CURRENT_USER\Software\Microsoft\Exchange
If this parameter is not set, Outlook may repeatedly prompt for a password or encounter issues with a blank login window.
Verifying Modern Authentication Usage in Outlook Client
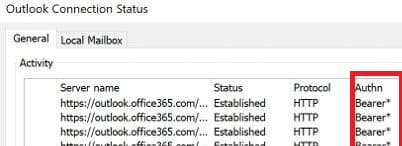
To confirm that the Outlook client is using Modern Authentication:
– Hold Ctrl and click the Outlook icon in the system tray.
– Ensure the Authn field displays Bearer*. This indicates the client is using Modern Authentication.
Transitioning to Modern Authentication in Microsoft 365 provides a higher level of security and support for modern authentication methods, such as Multi-Factor Authentication. It is recommended to promptly migrate all applications and users to Modern Authentication to avoid access issues and enhance data protection.