Windows file system audit policies allow you to track all access events for specific files and folders on a disk. Using audit policies, you can monitor events related to the creation, reading, modification, and deletion of files and folders on an NTFS file system in Windows. File auditing is commonly used to control access and changes to shared network folders accessed by multiple users simultaneously.
Enabling the File System Object Access Audit Policy
By default, auditing of file and folder access events is disabled in Windows. You can enable it using Group Policy. For configuration on a single server, use the Local Group Policy Editor (gpedit.msc). For domain-wide implementation in Active Directory, use the Group Policy Management Console (gpmc.msc).
1. Open the Group Policy Editor and navigate to:
Windows Settings > Security Settings > Advanced Audit Policy Configuration > System Audit Policies > Object Access
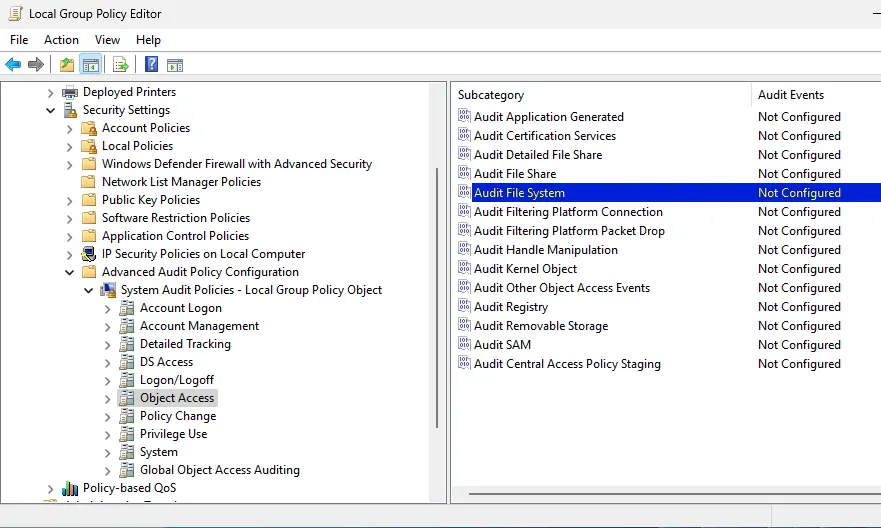
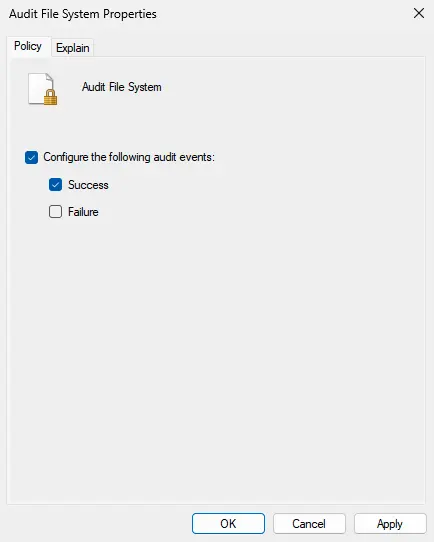
2. Open the File System policy and specify that you want to log only successful access events (Configure the following audit events -> Success).
3. Save the changes and update the local Group Policy settings using the command:
gpupdate /force
You can also enable auditing from the command line. List available audit categories:
AuditPol.exe /list /subcategory:*
Enable auditing of successful file system object access events:
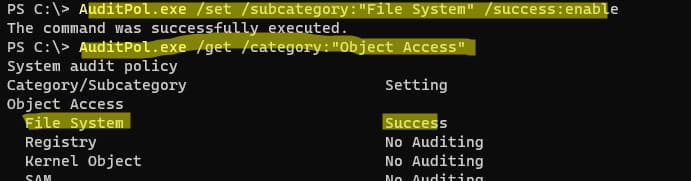
AuditPol.exe /set /subcategory:"File System" /success:enable
View the audit category settings:
AuditPol.exe /get /category:"Object Access"
Configuring Audit Events for Files and Folders
After enabling the audit policy, configure audit settings for the specific files and folders you want to monitor. For example, to track read, modify, and create events in the C:\Docs directory:
1. Open the folder’s properties and navigate to Security > Advanced > Auditing.
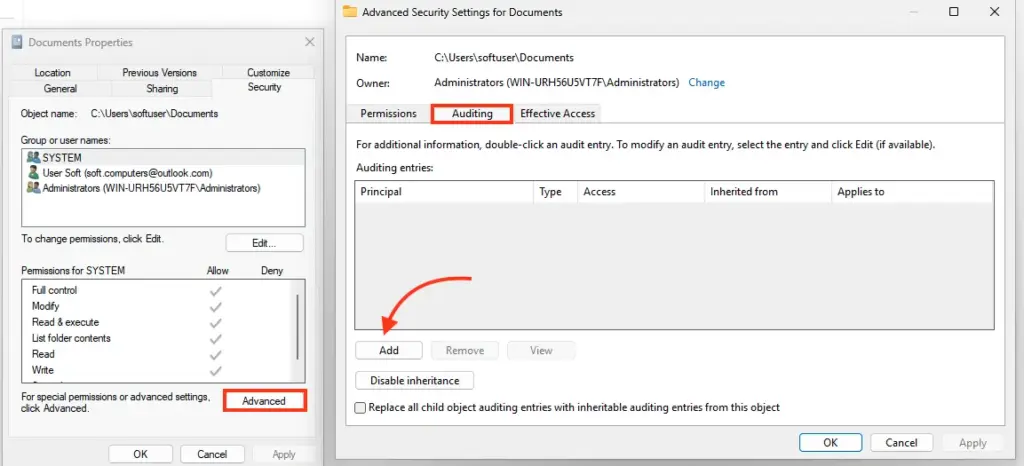
2. Click Add, and in the Principal field, select “Users” or “Everyone” to monitor their events.
3. In the Type list, specify that only successful events should be audited (Success).
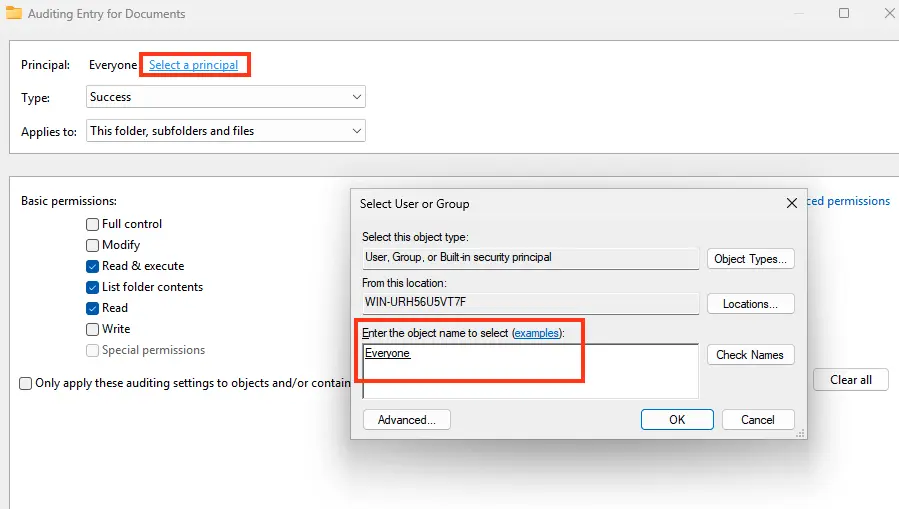
4. In Applies to, choose which objects to audit (by default, this folder, subfolders, and files).
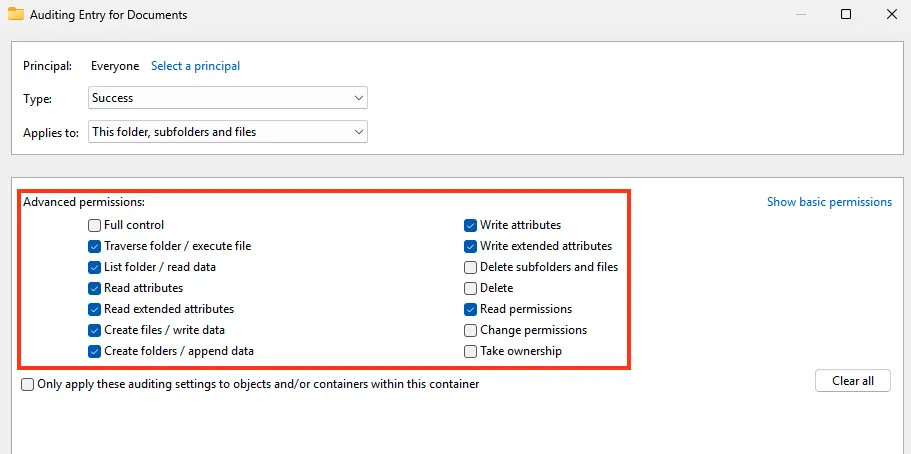
5. In Advanced Permissions, select the actions to monitor, such as reading (List folder/read data) and modifying files (Create files/folders, write data).
You can enable auditing for a directory using PowerShell:
$Path = "C:\Docs"
$AuditChangesRules = New-Object System.Security.AccessControl.FileSystemAuditRule('BUILTIN\Users', 'Delete,DeleteSubdirectoriesAndFiles', 'none', 'none', 'Success')
$Acl = Get-Acl -Path $Path
$Acl.AddAuditRule($AuditChangesRules)
Set-Acl -Path $Path -AclObject $Acl
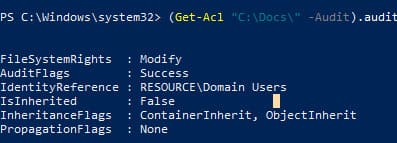
View the folder’s audit settings using PowerShell:
(Get-Acl "C:\Docs\" -Audit).Audit
To recursively scan all directories and find folders with file system auditing enabled, use the following script:
$folders=Get-ChildItem "c:\docs" -Recurse |Where-Object {$_.PSIsContainer}
foreach ($folder in $folders)
{
$auditacl=(Get-Acl $folder.FullName -Audit).audit
if ($auditacl -ne "") {write-host $folder.FullName}
}
Viewing File and Folder Access Audit Events
Once actions are performed on files in the specified folder, the audit policy logs them in Event Viewer. To view the events:
1. Launch Event Viewer (eventvwr.msc).
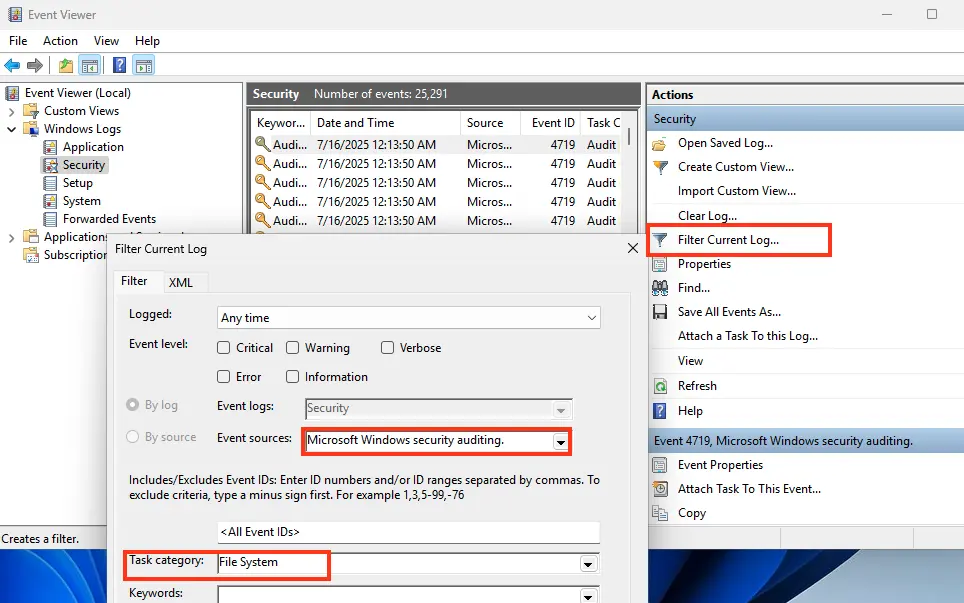
2. Navigate to Windows Logs > Security and filter the log by source:
Event Source: Microsoft Windows security audit
Task Category: File System
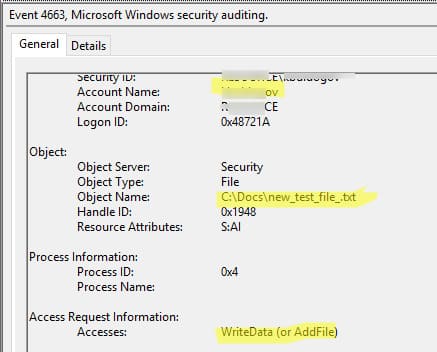
Events with Event ID 4663 contain information about the user who performed the action, the file name, and the type of operation (e.g., modification or deletion).
Using PowerShell to Retrieve Audit Events
To retrieve all events related to a specific object, use the following PowerShell script:
$fileName = "C:\\docs\\13131.txt"
$results = Get-WinEvent -FilterHashtable @{logname='Security'; id=4663,4659} |`
Where-Object { $_.message -match $fileName -and $_.message -notmatch "Имя учетной записи:\s*машина$*"}`
foreach ($result in $results) {
$Account = $result.properties[1].Value
$objectName = $result.properties[6].Value
$accessMask = $result.properties[8].Value
if ( $accessMask -like "*00000000-*") { $accessMask=$result.properties[9].Value}
$accessMask2 = $result.properties[9].Value
$fileOperation = ""
switch -Wildcard ($accessMask) {
"*%%1538*" { $fileOperation = "READ_CONTROL" }
"*%%4416*" { $fileOperation = "Read data (or list directory)" }
"*%%4417*" { $fileOperation = "Write data (or add file)" }
"*%%4418*" { $fileOperation = "Append data (or add subfolder or create pipe)" }
"*%%4419*" { $fileOperation = "Read extended attributes" }
"*%%4420*" { $fileOperation = "Write extended attributes" }
"*%%4423*" { $fileOperation = "Read attributes" }
"*%%4424*" { $fileOperation = "Write attributes" }
"*%%4426*" { $fileOperation = "Delete" }
"*%%4428*" { $fileOperation = "Read permissions" }
"*%%4429*" { $fileOperation = "Write DAC" }
"*%%4430*" { $fileOperation = "Write owner" }
"*%%4432*" { $fileOperation = "Synchronize" }
"*%%4433*" { $fileOperation = "Access system security" }
"*%%4434*" { $fileOperation = "Maximum allowed access" }
"*%%4436*" { $fileOperation = "Full control" }
"*%%4437*" { $fileOperation = "Execute" }
"*%%4438*" { $fileOperation = "Write" }
"*%%4439*" { $fileOperation = "Read" }
"*%%1537*" { $fileOperation = "Delete" }
default { $fileOperation = "Unknown" }
}
Write-Host $result.Id $result.TimeCreated $Account $objectName $fileOperation
}
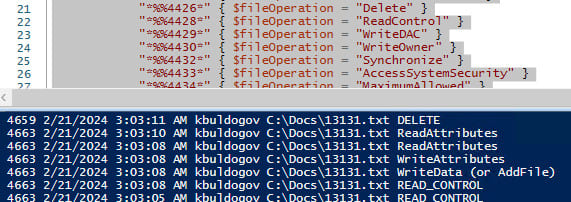
This script will display all actions performed on the specified file that were recorded by Windows audit policies.