This article explains how to resolve an authentication error when connecting to a Remote Desktop via RDP, which occurs when using a vulnerable version of the CredSSP protocol.
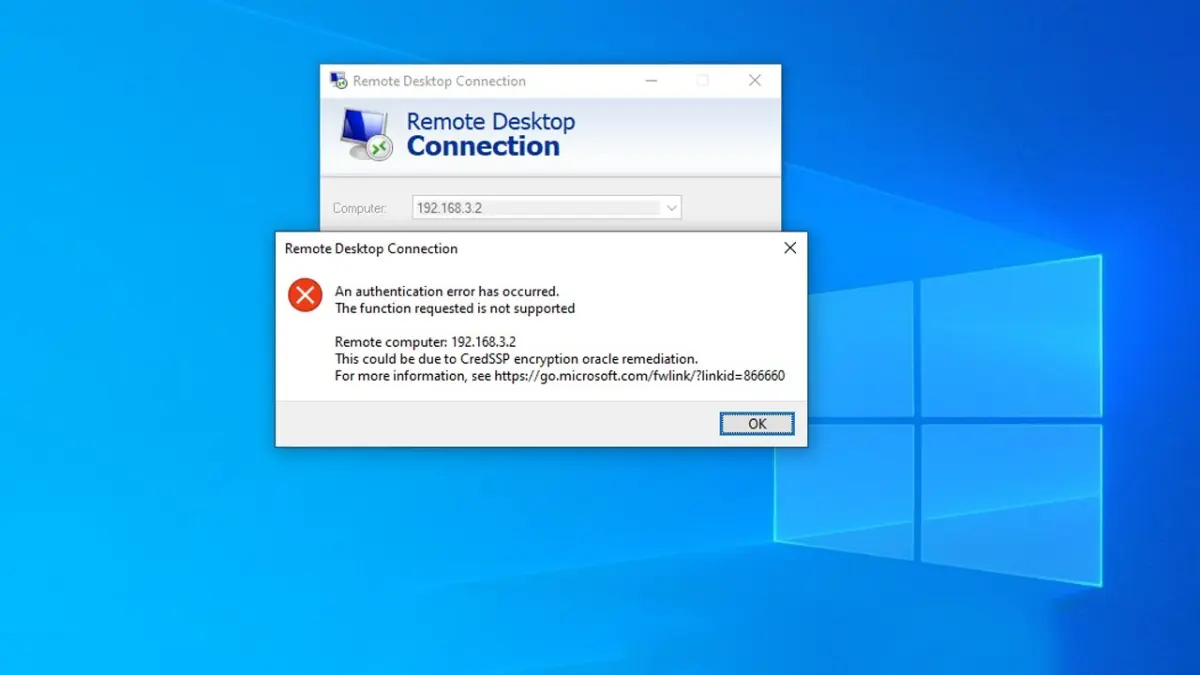
When connecting to a remote computer’s desktop using the built-in RDP client (mstsc.exe), you may encounter the error:
An authentication error has occurred. The function requested is not supported
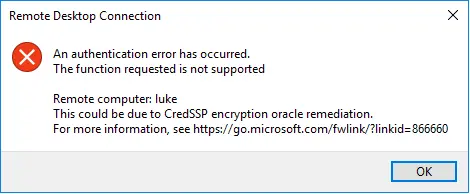
Cause of the RDP Authentication Error
This error occurs because Windows blocks RDP connections to remote computers using a vulnerable version of the CredSSP protocol (CVE-2018-0886). The Credential Security Support Provider (CredSSP) protocol is used for pre-authentication when Network Level Authentication (NLA) is enabled for RDP access. Microsoft released an update to address this vulnerability in 2018 (CredSSP update). However, if this update is not installed on the remote host, this error may appear.
Fixing the RDP Authentication Error
To resolve the error and connect to your RDP server, use one of the following methods:
Recommended Method
1. Install the latest cumulative Windows security updates on the remote computer or server you are connecting to via RDP. The computer may have been deployed from an outdated image or has Windows Update disabled.
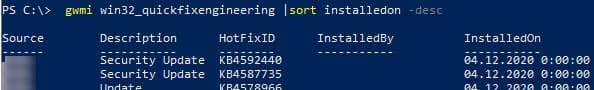
2. Check the date of the last installed Windows update using the PSWindowsUpdate module or the command:
gwmi win32_quickfixengineering | sort installedon -desc
3. Obtain updates via Windows Update or download and install them manually. Install any cumulative update released after 2019.
Not Recommended — Temporary Method 1
– Allow connections to RDP servers with an insecure version of CredSSP on your client computer by modifying the AllowEncryptionOracle registry key:
REG ADD HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\CredSSP\Parameters /v AllowEncryptionOracle /t REG_DWORD /d 2
– Alternatively, modify the Encryption Oracle Remediation local policy, setting it to Vulnerable.
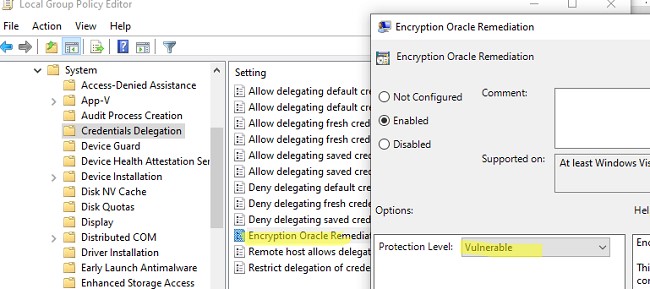
– After successfully connecting and updating the server, disable the policy or revert the AllowEncryptionOracle key to 0:
REG ADD HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\CredSSP\Parameters /v AllowEncryptionOracle /t REG_DWORD /d 0
Not Recommended — Temporary Method 2
– Disable Network Level Authentication (NLA) on the RDP server.
Disabling Network Level Authentication (NLA) for RDP
If NLA is enabled on the RDP server, the CredSSP protocol is used for user pre-authentication. You can disable Network Level Authentication in the system properties (SystemPropertiesRemote.exe) under the Remote tab by unchecking Allow connections only from computers running Remote Desktop with Network Level Authentication.
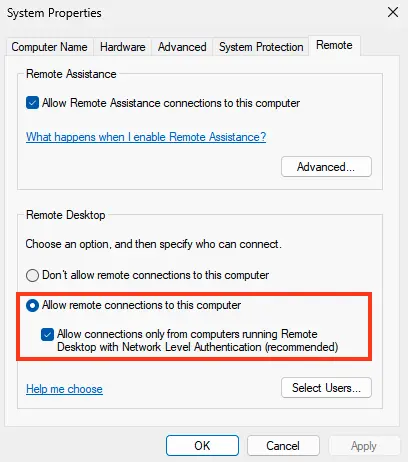
In Windows 7, this option is worded differently: Allow connections from computers running any version of Remote Desktop (less secure).
You can also disable NLA using the Local Group Policy Editor:
– Navigate to Computer Configuration > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Security.
– Disable the policy Require user authentication for remote connections by using Network Level Authentication.
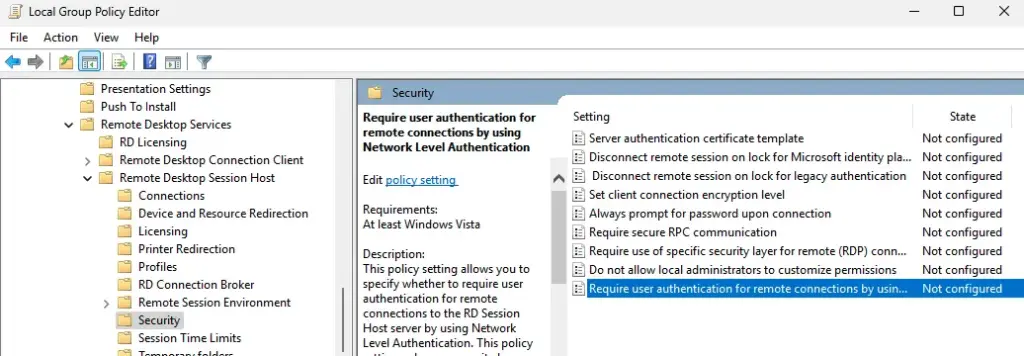
Additionally, in the policy Require use of specific security layer for remote (RDP) connections, set the Security Layer to RDP.
To apply the new RDP settings, update group policies:
gpupdate /force
Alternatively, reboot the computer. After this, you should be able to connect to the remote desktop successfully.