This article explains how to enable the Transport Layer Security (TLS 1.2) protocol in various versions of Windows, including support for .NET and WinHTTP applications. Since TLS 1.0 and TLS 1.1 are deprecated, ensuring TLS 1.2 support on all Windows clients and servers is critical.
In modern versions of Windows (11, 10, 8.1, and Windows Server 2022/2019/2016/2012R2), TLS 1.2 is enabled by default. However, enabling TLS 1.2 in Windows 7, Windows Server 2008R2, and Windows Server 2012 requires several configuration steps.
Enabling TLS 1.2 in Windows 7
1. Install Service Pack 1 (SP1) for Windows 7 if it is not already installed.
2. Download and install update KB3140245 from the Microsoft Update Catalog.
3. Download and install the patch MicrosoftEasyFix51044.msi, which adds the necessary registry settings for TLS 1.2 support in Windows 7/2008R2/2012.
4. Reboot the computer.
These steps add the required registry parameters, such as DisabledByDefault = 0 and Enabled = 1, to the registry keys HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client and Server.
For applications using the WinHTTP API, add the parameter DefaultSecureProtocols = 0x00000A00 to the registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\WinHttp (for 64-bit Windows, use HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Internet Settings\WinHttp).
Possible Values for DefaultSecureProtocols
– 0x00000A0: Enables SSL 3.0 and TLS 1.0
– 0x0000AA0: Enables TLS 1.1 and TLS 1.2
– 0x00000A00: Enables only TLS 1.1 and TLS 1.2
– 0x00000800: Enables only TLS 1.2
PowerShell Script for Registry Configuration
$reg32bWinHttp = "HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\WinHttp"
$reg64bWinHttp = "HKLM:\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Internet Settings\WinHttp"
$regWinHttpDefault = "DefaultSecureProtocols"
$regWinHttpValue = "0x00000800"
$regTLS12Client = "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client"
$regTLS12Server = "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server"
$regTLSDefault = "DisabledByDefault"
$regTLSValue = "0x00000000"
$regTLSEnabled = "Enabled"
$regTLSEnableValue = "0x00000001"
For Windows x86:
$test = Test-Path -Path $reg32bWinHttp
if(-not($test)){
New-Item -Path $reg32bWinHttp
}
New-ItemProperty -Path $reg32bWinHttp -Name $regWinHttpDefault -Value $regWinHttpValue -PropertyType DWORD
For Windows x64:
$test = Test-Path -Path $reg64bWinHttp
if(-not($test)){
New-Item -Path $reg64bWinHttp
}
New-ItemProperty -Path $reg64bWinHttp -Name $regWinHttpDefault -Value $regWinHttpValue -PropertyType DWORDNew-Item -Path "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2"
New-Item -Path $regTLS12Client
New-Item -Path $regTLS12Server
New-ItemProperty -Path $regTLS12Client -Name $regTLSDefault -Value $regTLSValue -PropertyType DWORD
New-ItemProperty -Path $regTLS12Client -Name $regTLSEnabled -Value $regTLSEnableValue -PropertyType DWORD
New-ItemProperty -Path $regTLS12Server -Name $regTLSDefault -Value $regTLSValue -PropertyType DWORD
New-ItemProperty -Path $regTLS12Server -Name $regTLSEnabled -Value $regTLSEnableValue -PropertyType DWORD
Reboot the computer:
Restart-Computer
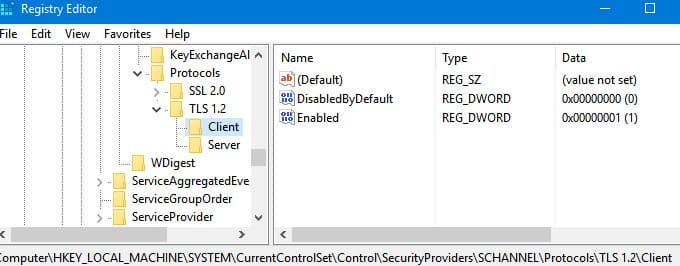
Enabling TLS 1.2 for .NET Framework Applications
To enable TLS 1.2 for .NET Framework applications, configure the registry to use system encryption protocols for .NET 3.5 and 4.x. If using .NET Framework 4.5.1 or 4.5.2 on Windows Server 2012 R2/2012 or Windows 8.1, install the latest updates for .NET Framework 4.5.1 first.
Registry Settings for .NET
For .NET 3.5 and 2.0:
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v2.0.50727] "SystemDefaultTlsVersions"=dword:00000001
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\.NETFramework\v2.0.50727] "SystemDefaultTlsVersions"=dword:00000001
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v2.0.50727] "SchUseStrongCrypto"=dword:00000001
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\.NETFramework\v2.0.50727] "SchUseStrongCrypto"=dword:00000001
For .NET 4.x:
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v4.0.30319] "SystemDefaultTlsVersions"=dword:00000001
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\.NETFramework\v4.0.30319] "SystemDefaultTlsVersions"=dword:00000001
For .NET 4.6:
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v4.0.30319] "SchUseStrongCrypto"=dword:00000001
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\.NETFramework\v4.0.30319] "SchUseStrongCrypto"=dword:00000001
For example, without these settings, PowerShell cannot connect to PSGallery repositories on Windows Server 2012 R2 due to reliance on the deprecated TLS 1.0 protocol.
Using IISCrypto
To manage TLS/SSL protocols and SChannel settings, use the free IISCrypto utility. It allows enabling or disabling protocol versions via a graphical interface. Note that IISCrypto does not modify TLS settings for .NET or WinHTTP.
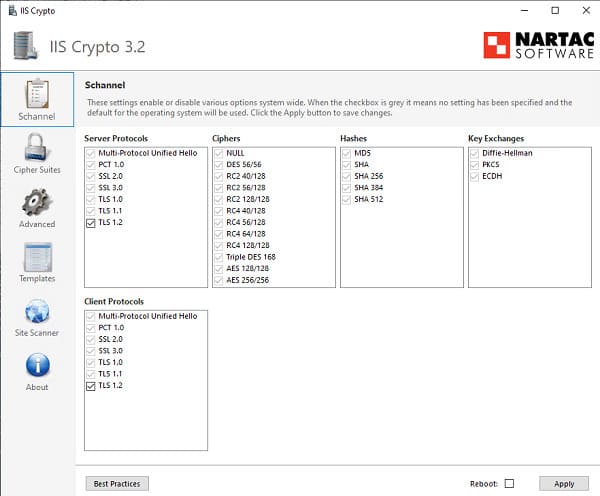
After applying these configurations, TLS 1.2 will be enabled in Windows 7, ensuring secure communications. This is particularly important for supporting modern applications and services requiring enhanced security.