This article explains how to install and configure a built-in OpenSSH server in Windows 10/11 and Windows Server 2022/2019. You will learn how to connect to the system using the secure SSH protocol, similar to how it is done in Linux.
Installing the OpenSSH Server in Windows
The OpenSSH server is included in modern versions of Windows 10 (starting from build 1803), Windows 11, and Windows Server 2022/2019 as a Feature on Demand (FoD). You can install it in several ways.
1. Installation via PowerShell:
Get-WindowsCapability -Online | Where-Object Name -like 'OpenSSH.Server*' | Add-WindowsCapability -Online
2. Installation via DISM:
dism /Online /Add-Capability /CapabilityName:OpenSSH.Server~~~~0.0.1.0
3. Installation via Settings:
– Go to Settings -> Apps -> Optional features -> Add a feature.
– Find OpenSSH Server and click Install.
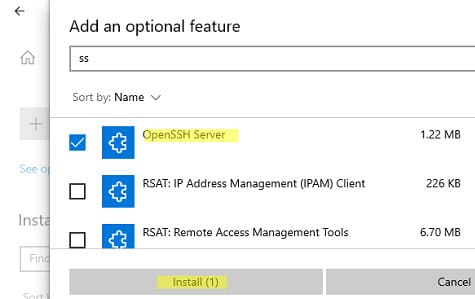
4. Installation via MSI Package:
You can install OpenSSH using an MSI installer available on GitHub:
Invoke-WebRequest https://github.com/PowerShell/Win32-OpenSSH/releases/download/v8.9.1.0p1-Beta/OpenSSH-Win64-v8.9.1.0.msi -OutFile $HOME\Downloads\OpenSSH-Win64-v8.9.1.0.msi -UseBasicParsing
msiexec /i c:\users\root\downloads\OpenSSH-Win64-v8.9.1.0.msi
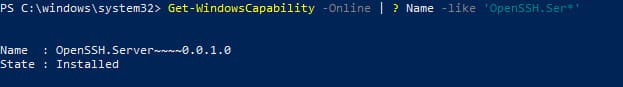
To verify that the OpenSSH server is installed, run:
Get-WindowsCapability -Online | ? Name -like 'OpenSSH.Ser*'
State: Installed
Configuring the SSH Server in Windows
After installing OpenSSH, two services are created in Windows:
– ssh-agent (for managing keys if you configured SSH key-based authentication)
– sshd (the SSH server itself)
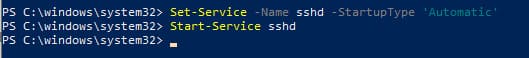
1. Configuring Automatic Startup of the SSH Service:
Run the following PowerShell commands to enable automatic startup of the SSH server:
Set-Service -Name sshd -StartupType 'Automatic'
Start-Service sshd
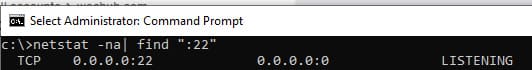
2. Checking the SSH Port:
Ensure the server is listening on TCP port 22:
netstat -na | find ":22"
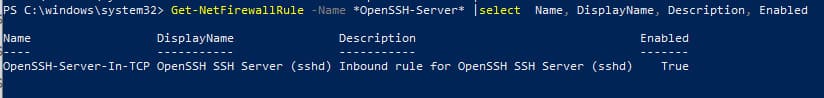
3. Configuring the Firewall:
Verify that the firewall allows SSH connections:
Get-NetFirewallRule -Name *OpenSSH-Server* | select Name, DisplayName, Description, Enabled
If the rule is disabled, enable it:
New-NetFirewallRule -Name sshd -DisplayName 'OpenSSH Server (sshd)' -Enabled True -Direction Inbound -Protocol TCP -Action Allow -LocalPort 22
If the rule is disabled (Enabled=False) or missing, create a new inbound rule:
New-NetFirewallRule -Name sshd -DisplayName 'OpenSSH Server (sshd)' -Enabled True -Direction Inbound -Protocol TCP -Action Allow -LocalPort 22
Configuring the sshd_config File
The OpenSSH server configuration file is located at C:\ProgramData\ssh\sshd_config. You can edit it using any text editor. For example, open it with Notepad:
start-process notepad C:\ProgramData\ssh\sshd_config
1. Restricting Access for Users/Groups:
– Deny connections for a specific user:
DenyUsers softcomputers\admin@192.168.1.10
DenyUsers corp\*
– Allow access only for a local group:
AllowGroups sshadmins
2. Changing the SSH Port:
To change the port, modify the Port directive. After making changes, restart the service:
Restart-Service sshd
3. Allowing Access for a Specific Domain Group:
AllowGroups softcomputers\sshadmins
By default, all Windows users can connect to the OpenSSH server. Directives are processed in the following order: DenyUsers, AllowUsers, DenyGroups, AllowGroups.
4. Denying Access for Administrator Accounts:
To perform privileged actions in an SSH session, you can use runas:
DenyGroups Administrators
The following directives enable SSH access via keys and passwords:
PubkeyAuthentication yes
PasswordAuthentication yes
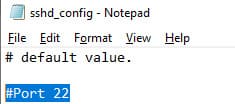
5. Changing the Default SSH Port (TCP/22):
Modify the Port directive in the sshd_config file to change the port on which OpenSSH accepts connections.
6. Restarting the sshd Service After Configuration Changes:
After modifying the sshd_config file, restart the sshd service:
Restart-Service sshd
Connecting to a Windows Computer via SSH
You can connect to Windows via SSH using any SSH client (e.g., PuTTY or the built-in Windows SSH client). Example connection command:
ssh alexbel@192.168.31.102
In this example, alexbel is the username on the remote Windows computer, and 192.168.31.102 is the IP address or DNS name of the computer.
You can use the following Windows username formats for SSH connections:
alex@server1 – Local Windows user
alex@softcomputers.org@server1 – Active Directory user (UPN format) or Microsoft/Azure (Microsoft 365) account
softcomputers\alex@server1 – NetBIOS format
If using Kerberos authentication in a domain, enable it in the configuration file:
GSSAPIAuthentication yes
This allows seamless SSO authentication via Kerberos from a domain-joined Windows computer without entering a password:
ssh -K server1
Upon first connection, you will see a prompt to add the host to the list of known SSH hosts. Click “Yes”.
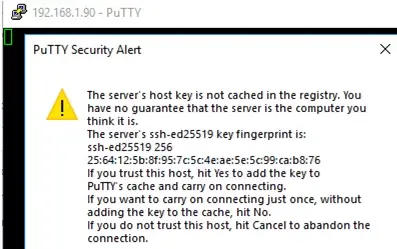
In the opened window, authenticate using a Windows user account.
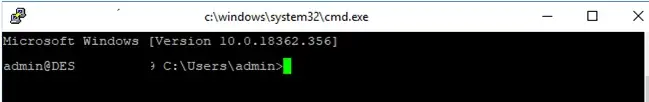
Upon successful connection, the cmd.exe command shell starts with a prompt:
admin@win10tst C:\Users\admin>
In the command line, you can execute various commands, run scripts, and launch applications.
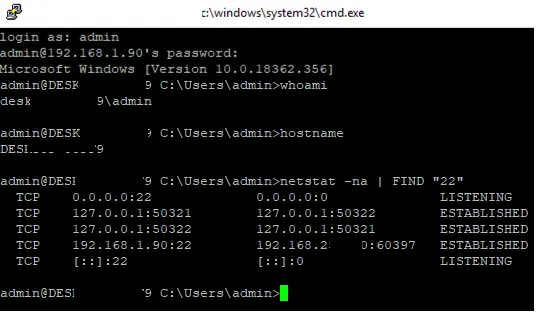
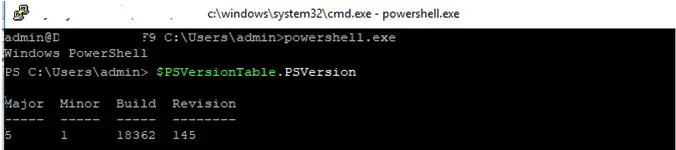
To start the PowerShell interpreter, run:
powershell.exe
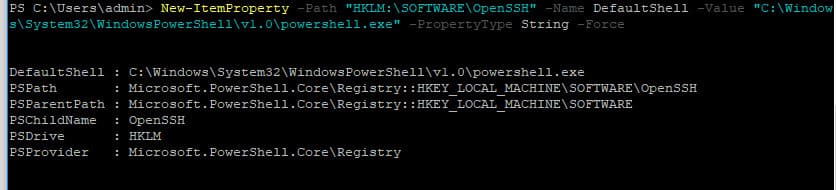
To change the default command shell in OpenSSH from cmd.exe to PowerShell, modify the registry with:
New-ItemProperty -Path "HKLM:\SOFTWARE\OpenSSH" -Name DefaultShell -Value "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -PropertyType String –Force
Reconnect to SSH and verify that the PowerShell command interpreter is used (indicated by the PS C:\Users\admin> prompt).
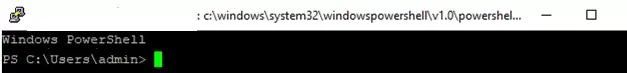
The SSH session now uses the PowerShell command line, supporting familiar features like autocompletion, syntax highlighting via the PSReadLine module, command history, and more. If the current user is part of the local Administrators group, all commands in their session run with elevated privileges, even with UAC enabled.
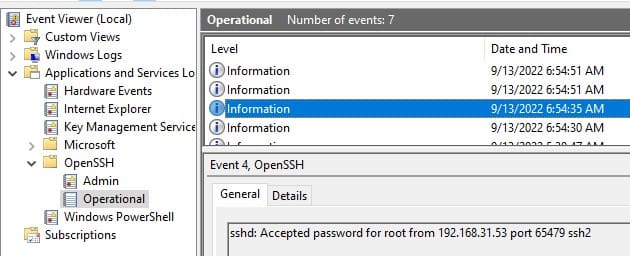
SSH Connection Logs in Windows
SSH connection logs are recorded in the Windows Event Log via Event Tracing for Windows (ETW). To view the logs:
1. Open Event Viewer by running eventvwr.msc.
2. Navigate to Application and Services Logs -> OpenSSH -> Operational.
Example of a successful password-based connection event:
EventID: 4
sshd: Accepted password for user1 from 192.168.31.102 port 55432 ssh2
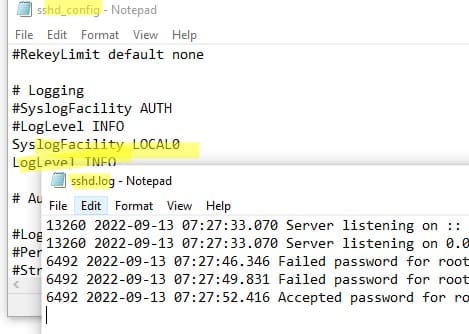
If needed, you can configure logging to a text file by adding the following directives to the sshd_config file:
SyslogFacility LOCAL0
LogLevel INFO
Restart the sshd service to apply changes and verify that SSH server logs are now written to C:\ProgramData\ssh\logs\sshd.log.
Now you know how to set up and use an OpenSSH server on Windows for secure remote access via the SSH protocol.